Information technology (IT) is no longer a tucked-away department with little impact on the success of a business. Organizations across industries need data storing, analysis and processing tools to manage every single aspect of their operations, so anything that affects their IT infrastructure carries some major risks. Read on to learn the importance of IT risk management.
What Is IT Risk Management?
IT risk management is a process that consists of identifying, assessing, prioritizing and managing IT risks. It’s a cross-functional effort that requires the coordination of multiple teams and is usually led by an IT risk manager.
Over the years, several IT risk management frameworks have been developed to help organizations with IT risk management. These IT risk management frameworks describe the guidelines, procedures and documentation that should be utilized to manage IT risks. In addition, IT risk management frameworks also set the standards that organizations should meet to comply with regulations such as international cybersecurity protocols.
What Is IT Risk?
The term IT risk refers to a variety of IT risks that can affect the IT environment of an organization, which is the infrastructure, hardware, software and networking that are utilized to run its IT operations.

Get your free
IT Risk Assessment Template
Use this free IT Risk Assessment Template for Excel to manage your projects better.
Common IT Risks Examples
The way that information technology is implemented varies from one organization to another, but in general terms, IT allows businesses to manage all the information that’s generated by their operations.
This information could be anything such as customer relationship management, market research, production planning or financial management data. Because of the importance of this data, a setback, limitation, risk, error or threat in IT can impact every facet of a business.
There are various internal and external threats that can affect the IT infrastructure of a business. Here are some examples of IT risks.
- Security risks: There are external IT risks that are caused by criminal activity such as malware, phishing, viruses and other types of cybersecurity risks.
- Physical threats: IT departments use servers, computers, networks and other physical resources to achieve their goals. Because they’re tangible elements, they are prone to natural disasters such as floods.
- Technical failures: Technical failures are the malfunction of IT elements such as a software bug, code errors and hardware failures, among other things.
- Human error: Users within the organization may make mistakes such as deleting data from a system unintentionally, failing to comply with cybersecurity policies or damaging hardware.
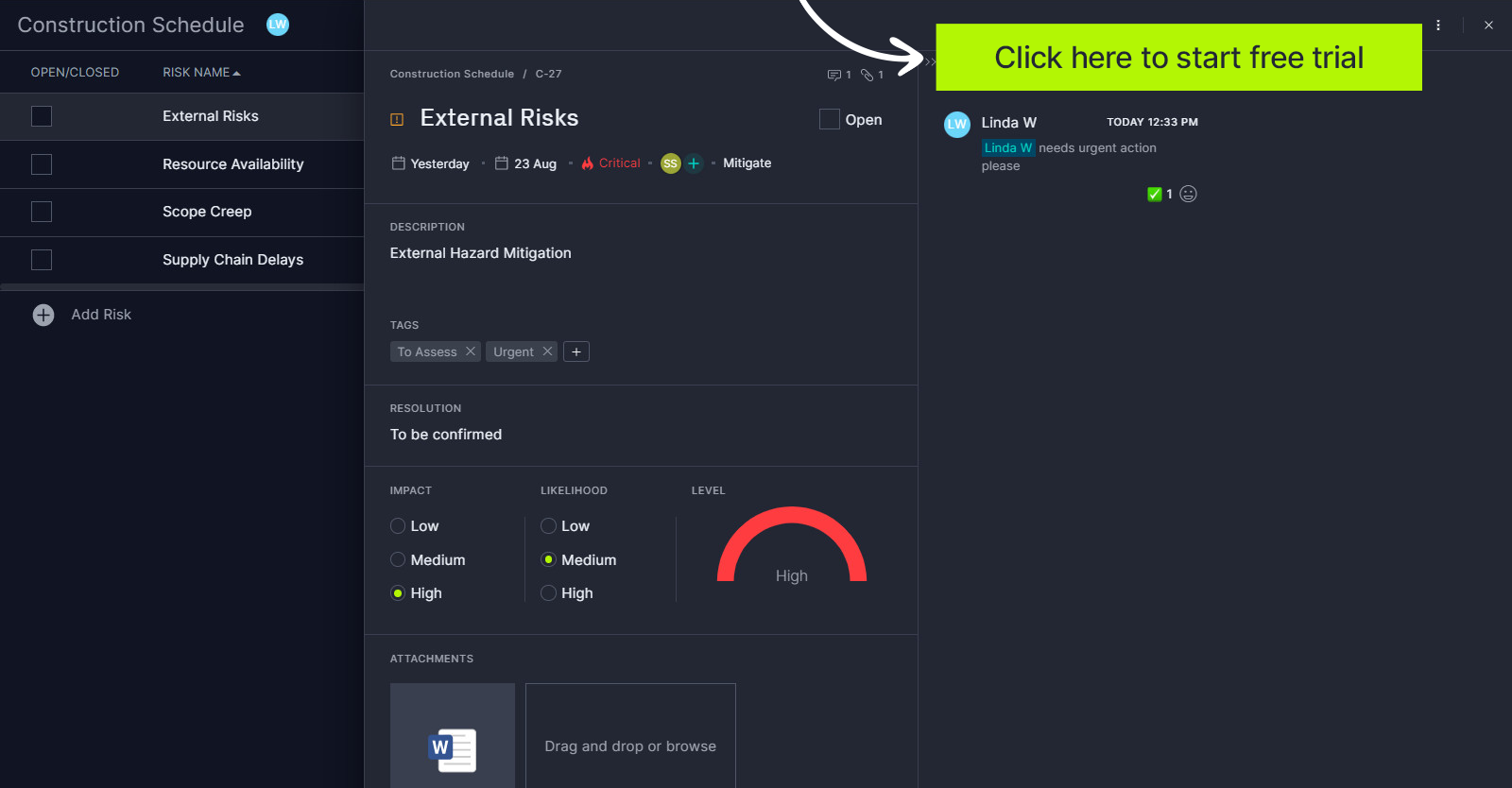
To mitigate negative outcomes, it’s worth investigating an IT project management software that can help you manage risks in IT and other projects. ProjectManager, for instance, lets you plan IT projects with either a Gantt chart, kanban board, task list or sheet, and then you can track your risks with our built-in risk tracker and matrix. It’s ideal for tracking IT risks, so you can respond quickly. Try it free!
Then there’s the problem of finding the right people to address IT risk management, those with training and expertise in the space. These people, ideally led by an IT risk manager, will also need to have a good work ethic so that they’re dependable and will commit to their responsibilities.
What Is an IT Risk Manager?
An IT risk manager is an IT professional who is very knowledgeable about risk management frameworks and is capable of identifying, assessing, and prioritizing IT risks. IT risk managers have the expertise to lead teams in executing risk management plans and developing risk mitigation strategies and policies to keep their organizations secure.
Top IT Risk Management Frameworks
As explained above, risk management frameworks help IT risk managers and teams know how to implement risk management practices to keep their IT operations safe. Here’s a quick overview of the most commonly used risk management frameworks there are.
NIST Risk Management Framework (RMF)
Developed by the National Institute of Standards and Technology (NIST), the NIST RMF is a risk management framework that focuses on cybersecurity and it’s usually implemented by larger organizations that have dedicated resources for IT risk management. This risk management framework consists of seven steps that summarize the process. To implement the NIST risk management framework it is important to be familiar with the NIST 800-53, a set of cybersecurity terms, measures and standards.
ISO 27001
The International Organization for Standardization (ISO) has developed the ISO 27001 risk management framework for those organizations that seek to obtain a global certification that allows them to demonstrate their capability to protect data such as intellectual property, financial information and any other sensitive information that’s shared by third parties such as customers, business partners or suppliers.
AICPA SOC 2
Created by the American Institute of CPAs (AICPA), the SOC 2 is a framework that helps organizations comply with cybersecurity standards for the processing of customer data. It consists of a series of steps that ensure that a business effectively complies with security, processing integrity, availability and confidentiality requirements.
OCTAVE FORTE
OCTAVE stands for Operationally Critical Threat, Asset, and Vulnerability Evaluation and is a risk management framework that helps organizations identify critical information technology assets, threats and vulnerabilities that could expose them to IT risks.
IT Risk Management Process
IT risk management is the application of risk management methods to information technology to manage the risks inherent in that space. To do that means assessing the business risks associated with the use, ownership, operation and adoption of IT in an organization. Follow these steps to manage risk with confidence.
1. Identify the Risk
You can’t prepare for risk without first figuring out, to the best of your ability, where and when it might arise. To do so you should conduct IT audits periodically and in addition establish a risk management culture in your organization that motivates IT managers and team members to be alert to uncovering and recognizing any risks.
2. Analyze the Risk
Once you’ve identified risk, you then must analyze it and discern if it’s big, small or minimal in its impact. Also, what would be the impact of each of the risks? You’ll then add these findings to your IT risk assessment report.
3. Evaluate and Rank the Risk
Once you evaluate the impact of risks and prioritize them, you can begin to develop strategies to control them. This is done by understanding what how risks can affect your IT infrastructure, which is determining the likelihood of it occurring and the magnitude of its impact. Then you can say that the risk must be addressed or can be ignored without causing major disruption to your IT operations. Again, these rankings would be added to your risk assessment.
4. Create an IT Risk Assessment Report
An IT risk assessment report will help you analyze security threats and what impact they might have on your organization. This allows IT security teams and other stakeholders to understand the risks and, in so doing, plan investments to secure weaknesses in one’s security.
5. Create an IT Risk Management Plan
The IT risk management plan is used to identify, evaluate and plan for risks that might show up in your organization. Specifically, it will outline the actions you’ll take to mitigate those risks, including costs, tools and what approaches will be used to identify, assess, mitigate and monitor those activities.
6. Respond to the Risk
After all this, if the risk becomes an actual issue, then you’re no longer in the theoretical realm. It’s time for action. This is what’s called risk response planning in which you take your high-priority risks and decide how to treat them or modify them, so they place as a lower priority. Risk mitigation strategies apply here, as well as preventive and contingency plans. Add these approaches to your risk assessment.
7. Monitor & Review the Risk
Once you act, you must track and review the progress of mitigating the risk. Use your risk assessment to track and monitor how your team is dealing with the risk to make sure that nothing is left out or forgotten.
8. Establish an IT Risk Management Policy
An IT risk management policy is a comprehensive overview of the governance of an organization and its employees’ usage and interaction with data and technology. It will include risk identification, risk measurement and assessment, risk mitigation, risk reporting and monitoring.

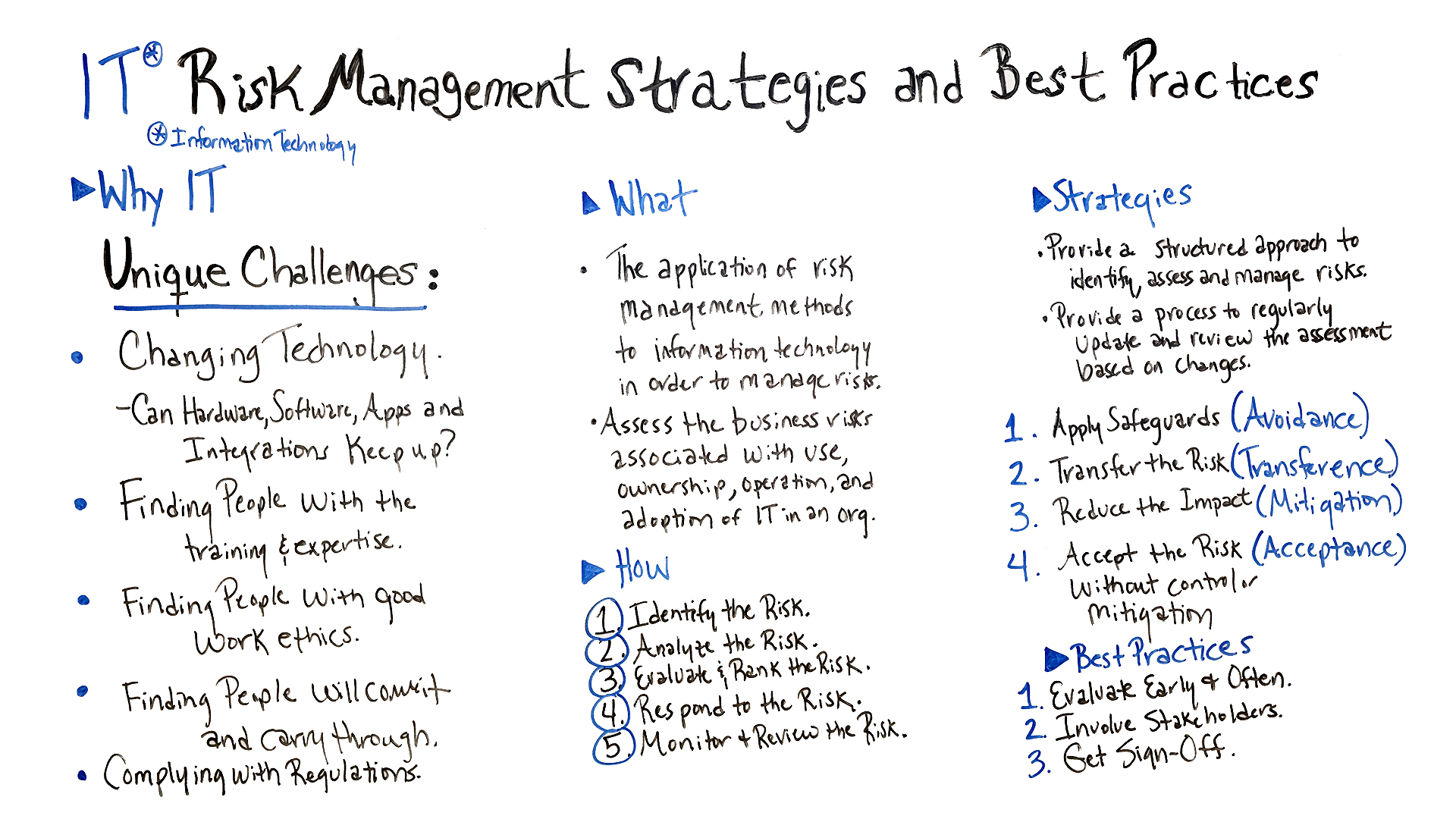
IT Risk Management Strategies
Strategies are a way to provide a structured approach to identify, access and manage risks. They provide a process to regularly update and review the assessment based on changes.
Apply Safeguards
This is an avoidance strategy, where the company decides to avoid risk at all costs and focuses a lot of resources on that end. If you can avoid the risk, then it is no longer a threat to the IT infrastructure. However, there is a downside to this. If you avoid the risk, you also avoid the associated potential of its return and opportunity. So, it’s a decision not to take lightly.
Transfer the Risk
This is a transference strategy when the company transfers the risk to another entity. This redistribution can be onto the company members, some outsource entity or an insurance policy.
Reduce the Impact
This is a mitigation strategy, where the company works to reduce the impact of the risk through methodology, teams or whatever resources are at its disposal. It can involve small changes but always must come by process and a plan.
Related: 15 Free IT Project Management Templates for Excel & Word
Accept the Risk
This is an acceptable strategy, where you know there is risk and accept that, so when and if it occurs you can deal with it then and there. This is sometimes unavoidable, but manageable if you follow the steps on your IT risk management plan.
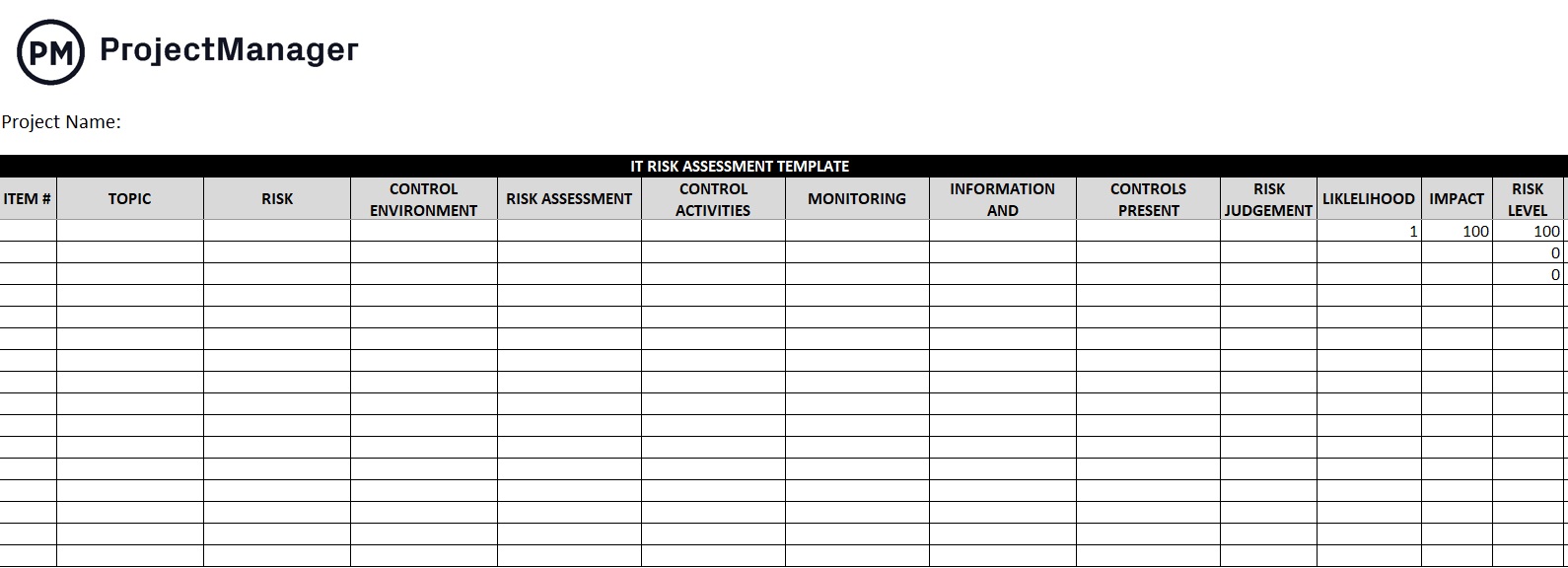
IT Risk Assessment Template
This free IT risk assessment template is ideal to document all the potential risks that might affect your IT infrastructure. Use it as you execute a new IT project or as part of IT audits.
More IT Risk Management Templates
Using IT risk management templates is an ideal way to standardize your IT audits and IT project planning efforts. Here are a few of the free IT project management templates you can use to manage IT risk.
Risk Register Template
A risk register, risk log or risk tracking template is a document that allows project managers, IT auditors and IT risk managers list down any potential risks that might affect their organization.
Risk Matrix Template
You can use this risk matrix template to estimate the likelihood and potential impact of IT risks, which is the first step towards creating a risk mitigation plan or an IT disaster recovery plan.
Best Practices for IT Risk Management
Here are six best practices when managing risk in IT.
- Evaluate Early & Often: There’s no better time to start the risk management process than now, so begin early. Remember IT risk management is a process that should be planned, tracked and reported as a project. Then continue monitoring all the time. Risk never sleeps.
- Lead from the Top: Good leadership is many things. One aspect is developing a risk culture in the organization. That means valuing input from everyone, believing in the importance of acknowledging risk and keeping a positive attitude about responding.
- Communications: Having a clear channel to communicate risk throughout the organization is paramount to identifying and responding quickly and effectively to risk.
- Strong Policies: If there is not already a process and plan to deal with risk, you’re always going to be one step behind. This is again why a project risk assessment is key, but so is understanding roles and responsibilities for everyone on the project team, having a continuity plan, etc.
- Involve Stakeholders: A great resource that is often overlooked are the project stakeholders, who have a unique perspective and can provide insight into areas where risk might arise. So, involve them throughout the process, from asking for their participation with the risk assessment template and over the whole course of the project.
- Get Signoffs: At every stage of your risk management, get people to sign off on the strategy, which includes the stakeholders.
IT Risk Management Certifications
There are risk management certifications that can show employers that you have a strong knowledge of the topic. For example, RIMS-CRMP certification shows performance ability, technical knowledge and commitment to quality as a certified risk management professional. There is also Certified in Risk and Information Systems Control (CRISC), offered by the Information Systems Audit and Control Association (ISACA), and others.
How ProjectManager Helps With IT Risk Management
ProjectManager is online project management software, which means that the data inputted is immediately updated, giving you the most accurate gauge to measure your project’s progress and catch any issues before they become risks.
Your risk assessment template can be uploaded into our online Gantt chart, where team members can receive assignments, comment and collect related documents, all of which can be attached to the risk.
Training Video on IT Risk Management Strategies
ProjectManager is a great tool, but it’s also a library of project management. We have tons of blog posts that speak to every aspect of the field and tutorial videos for a more visual approach.
Watch our resident expert Jennifer Bridges, PMP, as she explains IT management strategies and offers some best practices.
Here’s a screenshot for your reference.
Thanks for watching!
So, if you need a tool that can help you with your IT risk management, then sign up for our software now at ProjectManager.

